Access control credentials: So many choices, which one is best?

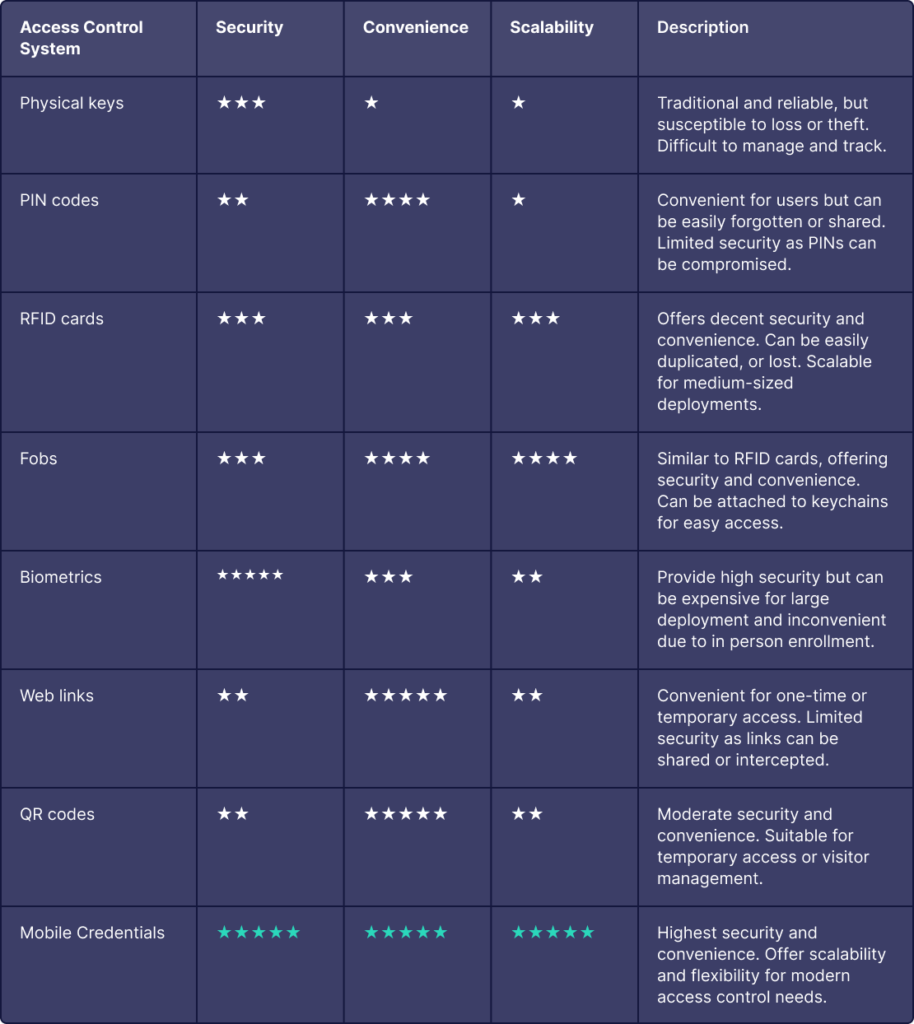
Choosing the right access control credentials is crucial for ensuring both the security and convenience of your spaces. Given today’s rapidly evolving landscape, organizations face a variety of options, each with distinct advantages and drawbacks. To assist in decision-making, we have compiled a comparative analysis of various access control systems, evaluating them on key criteria such as security, convenience, and scalability. This analysis ranges from traditional methods like physical keys to modern solutions like biometrics and mobile cards, providing insights to help you make an informed choice that meets your security needs and operational requirements.
Physical Keys
Physical keys are the traditional method of access control, involving mechanical keys that must be inserted into a lock to gain entry. Despite being reliable, they are increasingly seen as outdated due to their susceptibility to loss or theft and the logistical challenges they present in large organizations.
Pros:
- Simple and easy to use
- No need for electronic infrastructure
- Familiar and widely understood
Cons:
- Susceptible to loss, theft, and unauthorized duplication
- Difficult to manage and track
- Low scalability, especially for large organizations

PIN Codes
PIN codes involve users entering a personal identification number to gain access. They are commonly used in both residential and commercial settings due to their convenience. However, they face security challenges as PINs can be easily forgotten or shared.
Pros:
- Highly convenient for users
- No physical keys required
- Easy to implement and use
Cons:
- Can be easily forgotten or shared
- Limited security as PINs can be compromised
- Not scalable for large deployments

RFID Cards
RFID cards use radio-frequency identification technology to grant access when presented to a reader. They offer a balance of security and convenience and are widely used in corporate environments and medium-sized deployments. RFID card readers can often be upgraded to use more secure mobile credentials with devices like the Airfob Patch.
Pros:
- Convenient and easy to use
- Moderate security level — can be improved by using more expensive encrypted cards.
- Suitable for medium-sized deployments
Cons:
- Can be duplicated or lost
- Requires infrastructure for readers and cards
- Moderate scalability

Fobs
Similar to RFID cards, fobs are small devices that can be attached to keychains and used for access control. They offer the same convenience and security level as RFID cards but with the added benefit of being more portable and less likely to be forgotten.
Pros:
- Convenient and portable
- Easy to use and manage
- Moderate security level
Cons:
- Can be duplicated or lost
- Requires infrastructure for readers and fobs
- Moderate scalability

Biometrics
Biometric systems use unique physical characteristics, such as fingerprints or facial recognition, to verify identity and grant access. They provide high security but can be less convenient and more expensive to implement, especially on a large scale.
Pros:
- High security, difficult to forge or duplicate
- Eliminates the need for physical credentials
- Increasingly popular for high-security needs
Cons:
- Expensive to deploy, especially for large organizations
- In-person enrollment required
- Lower convenience due to setup requirements

Web Links
Web links provide a convenient method for temporary or one-time access by sending a link to the user. While highly convenient, they offer limited security and are not ideal for regular use. > Learn more
Pros:
- Highly convenient for temporary access
- No mobile app or physical credentials needed
- Easy to issue and manage
Cons:
- Limited security, links can be shared or intercepted
- Not suitable for long-term or high-security needs
- Moderate scalability
QR Codes
QR codes can be generated and scanned to grant access, making them useful for temporary access or visitor management. They offer moderate security and convenience, with the added benefit of being easily scalable. > Learn more
Pros:
- Easy to generate and scan
- Useful for temporary access or visitor management
- No mobile app or physical credentials needed
Cons:
- Can be shared or duplicated — can be mitigated somewhat with “dynamic” QR codes that change at regular intervals.
- Requires infrastructure for scanning
- Moderate scalability

Mobile Credentials
Mobile credentials, which are the solution of choice for Airfob, utilize smartphone technology to grant access, offering the highest levels of security, convenience, and scalability. Users can simply use their mobile devices to gain access, making this an ideal solution for modern access control needs. Are mobile credential secure?
Pros:
- High security and convenience
- Easily scalable for any size of deployment
- Leverages existing smartphone technology
Cons:
- Requires users to have a smartphone with remaining battery
- Can be dependent on mobile network connectivity
- Initial setup may require understanding how to use a smartphone

FREE EBOOK
Want to learn more about access control?

Download your
free eBook!
This eBook is not only for security experts. It’s also for business owners and anyone interested in the future of access control.